These days, information has enormous power. If you have access to sensitive data, you can do anything with it. It all depends on your imagination. As we know, all data is stored in databases. The reputation, efficiency, and profitability of many companies often depend on the private information they collect and store in databases. One of the most dangerous things that can happen to your database is a data breach. Information leaks not only threaten companies with reputational risks, but also with significant financial losses.
Recent research has shown that data privacy and access violations cost between $100 and $750 for each entry. The Uber app paid the largest fine for a data breach. The company paid a $148 million penalty after the cybercriminal released information about the breach. That’s why businesses must be proactive in building strong database security systems. To understand what we need to do to protect the database, we need to clarify what database security is.
- What is database security?
- Why database security is critical for your business
- Key database security issues
- Database security best practices
- Database protection techniques
- The role of database security in compliance
- Try dbForge Edge for comprehensive database security management
- Conclusion
What is database security?
Database security refers to the collective measures used to protect and secure a database or database management software from unauthorized use, malicious threats, and attacks. It encompasses a broad range of security processes, including access control, encryption, monitoring, and authentication, aimed at protecting the database from breaches, data leaks, and other forms of cyber threats.
Think of a database like a digital vault. It stores tons of important stuff—things like customer info, payment details, and business records. Now, imagine what could happen if that vault got broken into. That’s where database security management comes in. It’s all about locking that vault tight so hackers, viruses, or even careless employees can’t mess with what’s inside.
Core components of database security:
- Authentication is the process of verifying the identity of users or systems trying to access a database. It ensures that only authorized individuals can interact with the data. This is often done through passwords, usernames, or more secure methods like biometrics or two-factor authentication (2FA).
- Encryption is like writing your data in a secret code. If someone tries to steal it, they’ll only see a bunch of scrambled nonsense, unless they have the special key to decode it. This protects your info when it’s sitting in the database and when it’s traveling over the internet.
- Access control makes sure people only see the data they actually need for their job. Not everyone in a company needs access to everything. So, your marketing team might see customer emails, but not bank account details. It’s about limiting risk by giving the right access to the right people.
Why database security is critical for your business
With the increasing amount of sensitive information stored in databases, such as personal data, financial information, and intellectual property, the importance of database security and privacy has never been greater. A breach can have serious consequences, including financial loss, legal penalties, and damage to an organization’s reputation.
High cost of data breaches
When hackers get into your database, it’s not just a tech problem or one of the database security threats, it’s a business disaster. You could face lawsuits, government fines, and spend a fortune cleaning up the mess. On top of that, your company’s name could be dragged through the mud. Customers are quick to walk away if they feel their info isn’t safe.
Trust is everything
People want to know their data is in good hands. Strong DB security shows your customers that you take their privacy seriously. That trust can turn into repeat business, positive reviews, and a better reputation—all things that give you a competitive edge.
Keeping business running smoothly
Beyond protecting data, database privacy also keeps your day-to-day operations safe from disruption. A cyberattack can bring your systems to a halt, causing delays, lost revenue, and chaos for your team. With solid security in place, you can keep things running smoothly and stay focused on growth instead of damage control.
Key database security issues
Security isn’t just about avoiding leaks – it’s also about keeping your systems stable. A cyberattack can shut down operations, slow everything to a crawl, and cost you time and money. Solid security means fewer surprises and more time focusing on your actual business goals.
Some of the most common database security issues include:
- SQL injection attacks
- Insider threats
- Data breaches
- Poor access management.
Each of these issues can lead to stolen, lost, or altered data or other types of database attacks, causing damage to your operations, finances, and reputation.
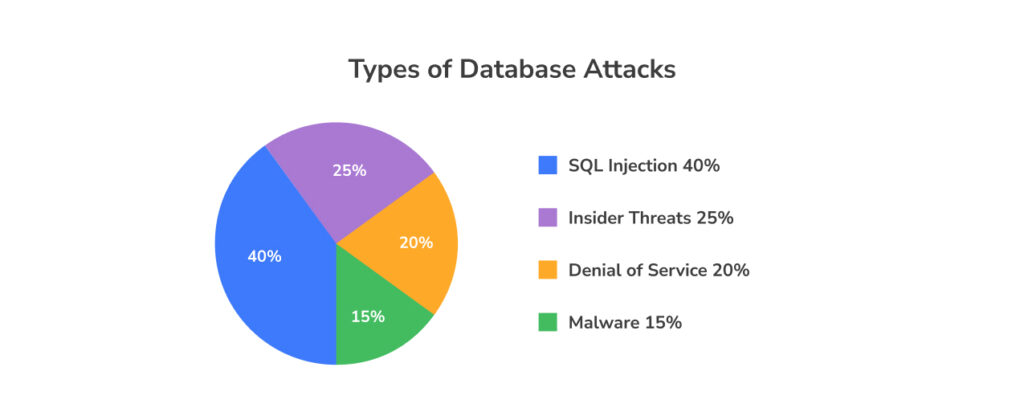
SQL injection attacks
An SQL injection involves manipulating the web application’s communication with the database. To do this, additional commands are injected into database queries, thus altering the query logic. SQL is the language used to communicate with the database. It is used (in slightly modified form) in various relational database systems (e.g., MySQL).
For example, instead of entering a name in a form, an attacker might enter a piece of code that urges the database to disclose secure data. If the database isn’t protected properly, it might actually do that.
Why it matters: A successful SQL injection can give attackers full control over your database. They could steal sensitive data, delete records, or even take down your whole system.
Insider threats
Not every threat comes from outside. Sometimes, the danger is already inside the company. Insider threats can come from employees, former staff, or contractors who have access to your database and either misuse it intentionally or accidentally.
For example, someone might copy sensitive customer data and sell it to a third party, or accidentally share a spreadsheet with confidential info.
Why it matters: Insiders often have trusted access, which makes it harder to detect their actions. These threats can be just as damaging (or worse) than external attacks.
Data breaches
A data breach is when sensitive information is accessed or exposed without authorization. This can happen through hacking, poor access controls, or even physical theft of servers and devices.
Why it matters: Breaches often lead to identity theft, legal action, and a loss of customer trust. Businesses may face fines, lawsuits, and long-term reputational damage. It’s not just about the loss of data—it’s about the loss of credibility.
Strong monitoring systems, regular audits, and limiting access to only those who truly need it are all critical steps in avoiding breaches.
Database security best practices
How to secure database? You don’t need to be a tech wizard to keep your database safe—you just need to follow a few smart habits. Even small mistakes (like skipping updates or using weak passwords) can leave the door wide open for hackers. Here’s how to stay one step ahead with database security best practices:
Regular software patching
Think of software updates like fixing cracks in your digital walls. Hackers love outdated systems because they already know how to break in.
Skipping updates gives cybercriminals an easy way in. Always install patches and updates as soon as they’re available.
Strong password policies
If your password is “1234” or “password,” you’re basically handing over the keys. Use long, complex passwords with a mix of letters, numbers, and symbols.
A complex password, especially when combined with two-factor authentication (2FA), is your first line of defense. It helps prevent both brute force attacks and casual snooping.
Regular backups and disaster recovery plans
Even with great security, things can still go wrong. That’s why backups are your safety net. If your system crashes or gets hacked, you won’t lose everything.
With regular backups and a disaster recovery plan, you can bounce back fast without starting from zero.
Security monitoring and auditing
Use tools that monitor who’s doing what in your database. Spotting strange activity early, like someone accessing files at 3 a.m., can stop a problem before it explodes.
Monitoring helps you catch threats, track access, and stay compliant with laws like GDPR. It’s like having security cameras for your data.
Database protection techniques
Securing a database isn’t about using one silver bullet solution. It’s about layering different protection techniques to cover every angle. Cyber threats can come from all directions, so a well-rounded defense strategy is essential. Combining tools like encryption, data masking, tokenization, and role-based access control can allow businesses to significantly reduce the risk of data exposure.
Data encryption
Encryption is one of the most powerful ways to protect sensitive data. It works by converting readable information into a coded format that can only be decoded with a specific key.
- At rest: Encrypting data stored in a database means that if someone gains access to the raw files, they still can’t read the actual data without the key.
- In transit: Encrypting data as it moves between systems (like from your database to a web app) protects it from being intercepted by attackers.
Even if hackers get their hands on your data, encryption makes sure it’s useless to them without the decryption key.
Data masking
Data masking is the process of hiding real data with fake but realistic values. It’s commonly used in testing and development environments where the actual data isn’t needed.
For example, a masked version of a credit card number might look like 4111-XXXX-XXXX-1234, keeping the format the same but hiding the real digits.
Developers and testers can work with data without exposing sensitive details, reducing the risk of leaks from non-production systems.
Role-based access control (RBAC)
RBAC is a fancy way of saying: “Not everyone in the company should see everything.” Instead of giving access to data based on who asks for it, you give access based on what someone does at work.
For example, someone in marketing might need customer contact info, but they have no reason to see payroll numbers or server settings. So, they don’t get access to those things.
Why this matters: It follows the “need-to-know” rule. The fewer people who can touch sensitive stuff, the lower the chance of someone messing it up, on purpose or by accident.
Each of these database protection techniques covers a different layer of security:
- Encryption protects data even if someone gets access to it.
- Masking prevents unnecessary exposure during testing.
- RBAC ensures that people only see what they’re supposed to.
Using them together builds a much stronger defense than relying on just one method. Think of it like locking your doors, setting an alarm, and using security cameras – you’re much safer with all three.
The role of database security in compliance
Protecting data isn’t just good practice, it’s the law. Regulations like GDPR, HIPAA, and PCI-DSS set strict rules on how personal and sensitive information should be handled. And at the heart of staying compliant with these rules is strong database security compliance.
If your business collects or stores customer data (payment info, health records, or personal details), you’re likely subject to one or more data protection laws. These laws are designed to keep people’s private information safe, and they come with serious consequences if you don’t follow them.
Failing to meet these requirements can lead to:
- Hefty fines
- Lawsuits
- Loss of customer trust
- Damage to your brand reputation.
Database protection provides the tools and practices needed to meet these regulations. Here’s how it supports compliance:
- Access control: Regulations like GDPR require that only authorized individuals can access personal data. Role-based access control (RBAC) and authentication help ensure this.
- Encryption: Many laws demand that sensitive data is encrypted both at rest and in transit. This protects it from unauthorized access, even if it’s stolen.
- Audit trails: Keeping detailed logs of who accessed what and when is essential for proving compliance. Database monitoring and logging tools make this possible.
- Data minimization and masking: These techniques help reduce the exposure of sensitive data, especially in non-production environments—a requirement under GDPR and similar laws.
Best practices for database security and compliance prove that database security management isn’t just a one-time checklist. It’s an ongoing process. It includes:
- Regular audits and security assessments
- Timely software patching
- Keeping up with changing regulations.
Try dbForge Edge for comprehensive database security management
As you can see, the importance of database security cannot be underestimated. Looking for a smart way to manage and secure your databases? dbForge Edge is a powerful all-in-one solution that helps you streamline database design, normalization, and security without the hassle.
How to secure database? With features like data encryption, activity monitoring, compliance checks, and role-based access control, dbForge Edge gives database administrators everything they need to keep sensitive data safe and meet various data security regulations.
It supports multiple database systems, offers a clean user interface, and helps reduce risks while saving time.
Try the free trial of dbForge Edge and see how it can simplify your database protection workflow.
Conclusion
92% of companies that experience data breaches report negative business impacts, reduced employee productivity, and diminished profits.
Don’t wait for a breach to take action. Start by reviewing your current setup, applying the best practices we’ve covered, and exploring tools like dbForge Edge to make your database security smarter and more efficient.
Protecting your data starts now—make it a priority with dbForge Edge.
FAQ
How can I improve database protection against security threats and vulnerabilities?
To improve database protection, start by strengthening your defenses across all access points. This includes enforcing strong password policies, regularly updating your software, and implementing robust authentication methods. Security monitoring tools are also crucial for detecting unusual behavior early. And keeping regular backups and having a recovery plan ensures that even if something goes wrong, your data can be restored quickly.
What are the common types of database attacks, and how can I prevent them?
Databases are often targeted by SQL injection attacks, insider threats, and data breaches caused by poor access controls. SQL injections occur when malicious code is inserted into database queries, while insider threats come from users with legitimate access who misuse it, either intentionally or by accident.
How can database security management help reduce risks associated with unauthorized access?
Database security management establishes the protocols and technologies that prevent unauthorized users from accessing or manipulating data. It ensures only the right people have access to specific data, often through role-based access controls. Authentication methods verify user identity, and encryption protects information from being readable even if it’s intercepted.
What is the role of encryption in database security, and how does it enhance database protection?
Encryption plays a vital role in keeping data safe by converting it into an unreadable format that can only be accessed with a specific decryption key. When data is encrypted both during storage and while being transmitted, even if cybercriminals manage to steal it, they won’t be able to make sense of it. This means sensitive information like personal records or financial data remains secure, adding a powerful layer of protection to your database infrastructure.
What are the key database security issues businesses should address to comply with industry regulations?
To stay compliant with regulations like GDPR, HIPAA, or PCI-DSS, businesses must focus on controlling who can access personal data, encrypting sensitive information, and maintaining detailed audit logs. These regulations require organizations to protect data from unauthorized use, prove they’ve done so, and minimize the amount of data that’s exposed in non-production environments.
How does dbForge Edge improve database security management for database administrators?
dbForge Edge strengthens the security management process by offering a range of tools tailored for database administrators. It supports secure data access and helps monitor user activity and revert changes whenever necessary.
What database protection features are included in dbForge Edge to secure sensitive business data?
In dbForge Edge, you’ll find features to backup and restore a database, handle and control user privileges, monitor connections, and trace user sessions, which can contribute to safeguarding business data. Apart from that, using Test Data Generator, you can handle development without letting unauthorized parties actually access private business client data.
How can dbForge Edge help implement database security best practices in my organization?
dbForge Edge makes it easier to apply best practices by combining key security features into one platform. It helps enforce password policies, automate updates, monitor activity, and manage permissions based on roles.

