What is Microsoft Entra ID, and why is this important in the database ecosystem?
If you have ever used the Microsoft Authenticator app, you’ve already seen how the MS Entra ID works, but only a fraction of it.
Microsoft Entra Identity (formerly Azure Active Directory) is a modern identity platform that unifies authentication, strengthens access controls, and integrates with the applications and databases businesses rely on most.
Think of this as a solid way to safeguard your information in the cloud beyond using the classic username and password, which, unfortunately, is prone to sophisticated threats like phishing, password spraying, and credential theft. Whether you are a developer, database analyst, or DBA, in this guide you will find out what Microsoft Entra ID is, how it works, and how dbForge Studio for SQL Server seamlessly integrates with Entra ID authentication, allowing you to connect to Azure SQL databases without relying on static credentials.
Let’s get right into it.
- What is Microsoft Entra ID?
- Authentication methods supported by Microsoft Entra ID
- How modern authentication works in Microsoft Entra ID
- Core identity features of Microsoft Entra ID
- Application and API authentication with Microsoft Entra ID
- Real-world use case: secure Azure SQL access via dbForge Studio
- Conclusion
- Frequently asked questions
What is Microsoft Entra ID?
According to Microsoft, the Entra ID is a cloud-based Identity and Access Management (IAM) platform. It provides a unified way to authenticate and authorize users, applications, and services across cloud and on-premises environments. However, Entra ID is not a completely new product; it was formerly referred to as Azure Active Directory (Azure AD) and rebranded on July 15, 2023. This move further reflects Microsoft’s broader Entra product family, which focuses on delivering a complete approach to identity, permissions, and network access.
Within Microsoft’s ecosystem, Entra ID plays a huge role in the Zero Trust security model. What this means is, with Zero Trust, instead of assuming internal networks are safe, every user and device is verified continuously. Entra ID provides the foundation for this verification method. It offers strong authentication, conditional access, and continuous monitoring, making it central to protecting modern hybrid enterprises.
Furthermore, Microsoft Entra Identity supports a wide range of authentication methods to fit different scenarios, from traditional username-and-password logins to modern passwordless options. Each method balances security, convenience, and compatibility.
The table provides details about the different authentication methods the MS Entra ID support.
| Authentication method | Credential type | User experience | Passwordless | Common use cases | Requires app registration |
|---|---|---|---|---|---|
| Username & Password | Username + Password | Basic login form | No | Legacy apps, internal portals | No |
| Multi-Factor Authentication | Password + Secondary Factor (e.g., app, SMS) | Login with extra verification step | No | Workforce access, high-risk users | Optional |
| Windows Hello for Business | Biometric or PIN + Trusted Device | Fast biometric/PIN login on device | Yes | Windows-based environments, enterprise logins | Yes |
| FIDO2 Security Key | Physical key + PIN | Tap device + PIN (no password) | Yes | Admins, shared machines, developer workstations | Yes |
| Microsoft Authenticator app | Push notification or app code | Tap approval or enter code | Yes | BYOD policies, remote access | Yes |
| Integrated Windows Auth (IWA) | Domain-joined account | Automatic login within corporate network | No | On-prem apps, internal network environments | No |
| Device code flow | Device code + browser login | Ideal for CLI, IoT, headless devices | Yes (can be) | Command-line tools, scripting environments | Yes |
Authentication methods supported by Microsoft Entra ID
From the preceding section, you have seen the different authentication methods the Microsoft Entra ID support. This section further breaks this down and explain how they work.
Username and password authentication
Authenticating with the classic username and password is very common. Almost all applications use this method. Within Entra ID, users sign in using their organizational credentials to access applications, cloud services, and resources. However, while this authentication method is simple and widely supported, it has significant limitations, which include weak or reused passwords. In worst-case scenarios, passwords can be stolen through phishing and brute-force attacks.
As a result, Microsoft Entra password protection relies heavily on enforcing strong password policies. Even with this, this method is less effective as a standalone defense.
Multi-factor authentication (MFA)
MFA is a popular security method in the database ecosystem. This authentication is used to add a second layer of protection beyond just password and username. When initiated, Microsoft Entra MFA strengthens security by requiring two or more verification factors before granting access. Without the verification factor, a user cannot log in. This added layer of security makes it harder for attackers to gain unauthorized access.
The supported Microsoft MFA methods include:
- SMS codes
- Phone calls
- Microsoft Authenticator app notifications or codes
Integrated Windows authentication
Integrated Windows Authentication (IWA) is another solid authentication method supported by the Microsoft Entra identity. However, it is designed for enterprises with on-premises infrastructure. IWA enables domain-joined devices to automatically authenticate users. This implies that employees working from their corporate laptops don’t have to type in their usernames and passwords repeatedly. The system recognizes the device, trusts the domain, and logs them in silently.
In addition, the real power of IWA shows when it is paired with Active Directory Federation Services (AD FS). This setup provides a smooth sign-in experience that extends beyond just on-premises resources. Users can access web applications, Microsoft 365 services, and even cloud-based apps without juggling multiple logins. It’s single sign-on (SSO) at enterprise scale.
For IT teams, IWA isn’t just about convenience. It ensures that authentication policies are centralized and consistent, giving administrators tighter control over who can access what, without sacrificing productivity for end users.
Passwordless authentication options
As stated earlier, password and username login can be compromised. Therefore, to eliminate this weakness, Entra ID supports a set of passwordless authentication methods that are secure, user-friendly, and aligned with the modern Zero Trust strategies. Here are some of these options.
- Windows hello for business: This method uses biometrics (such as fingerprint or facial recognition) or a device PIN tied to a trusted device. Credentials are stored securely on the device, making logins faster and resistant to phishing.
- Microsoft Authenticator app: If you use Microsoft Azure, you most likely use this authentication method. Microsoft Authenticator app provides passwordless sign-in via push notifications or verification codes. With this, you simply approve a request on your mobile device to confirm identity.
- FIDO2 security keys: These are hardware-based keys that support modern cryptographic standards. With this method, you just tap the key and enter a PIN. The FIDO2 security key offers strong, phishing-resistant authentication for shared devices, administrative accounts, or developer environments.
How modern authentication works in Microsoft Entra ID
No doubt, the MS Entra ID ensure secure resource access through industry-standard authentication protocols like the OAuth 2.0 and OpenID Connect (OIDC).
MS Entra ID enables secure, token-based access across apps, APIs, and services. With this, instead of transmitting or storing passwords, the Entra ID authentication relies on cryptographically signed tokens that validate user identity and grant time-limited access to resources. This approach is essential for securing cloud-native and hybrid environments, especially when combined with Microsoft Entra multifactor authentication and conditional access policies.
Let’s see how these modern authentication methods work on Microsoft Entra ID.
Token-based authentication flow
At the core of the Microsoft Entra integrated authentication method is a token-based flow, which ensures that credentials are never shared directly with applications. The table below presents a simplified step-by-step view of how this flow works in MS Entra ID.
| Step | Action | Description |
|---|---|---|
| 1 | Login request | A user attempts to sign in through an app or service. |
| 2 | Authorization | Entra ID connects and validates credentials and may enforce MFA or conditional access. |
| 3 | Token issuance | On success, Entra ID issues any of the following: • Access Token: used to access resources • ID Token: confirms the user’s identity |
| 4 | API access | The app presents the token to the target service (e.g., Azure SQL Database, Microsoft Graph API), which validates it before granting access. |
This token-driven process reduces the risk of theft or replay attacks.
Native app flow example (Microsoft Teams or dbForge Studio)
Native applications integrate with Entra ID using the same principles. For instance, a user can connect to Azure SQL database using dbForge Studio for SQL Server. The table below shows how this flow works.
| Step | Action | Description |
|---|---|---|
| 1 | Redirect to Microsoft sign-in | A user connects to the Azure SQL database through the dbForge Studio for SQL Server, and dbForge redirects the user to Microsoft’s secure login page. |
| 2 | MFA challenge (if required) | User verifies identity via Microsoft Authenticator, SMS code, or biometric login. |
| 3 | Access granted | Entra ID issues tokens, which dbForge Studio uses to establish a secure connection to Azure SQL Database. |
This flow enables seamless, passwordless, and secure access, without storing or transmitting sensitive credentials.
Federation with AD FS
In many hybrid setups, organizations rely on Active Directory Federation Services (AD FS) to connect their on-premises identity systems with Microsoft Entra ID. See the table below for how the flow works.
| Step | Action | Description |
|---|---|---|
| 1 | Authentication request redirect | A user from a federated domain tries to sign in, and Entra ID redirects the request to the organization’s AD FS server |
| 2 | Credential validation | AD FS checks the credentials against Active Directory, applies local security policies, and issues a validated token back to Entra ID. |
| 3 | Cloud token issuance | With that confirmation, Entra ID issues cloud-based tokens, enabling single sign-on (SSO) across on-premises and cloud resources. |
This federation model gives you a familiar and consistent login experience, lets domain-joined accounts use their existing corporate credentials, and makes SSO possible across hybrid enterprise environments.
Core identity features of Microsoft Entra ID
What are the core identity features that make the Microsoft Entra ID as effective as it is?
Let’s break them down.
Conditional access policies
Conditional access is the decision-making engine of Entra ID. Each time a user tries to sign in, Entra evaluates multiple signals such as the user’s identity, the device they are on, their geographic location, and the risk level of the sign-in attempt. Based on these factors, it can enforce the following policies:
- Allow access if conditions are trusted
- Require multifactor authentication for higher-risk logins
- Block access entirely if the risk is too high
This adaptive model tailors security to the context of each session, tightening defenses when risks are detected while keeping access simple for legitimate users.
Self-Service Password Reset (SSPR)
SSPR is another core feature of the Microsoft Entra ID that allows users to securely reset or unlock their accounts without waiting for IT support. MS Entra ID integrates SSPR into its standard authentication flows, prompting users to verify their identity using registered methods (such as Microsoft Authenticator or SMS). This approach reduces help desk overhead while empowering users to quickly regain access, all within a secure, policy-driven process.
Smart lockout & password protection
If you’re wondering how the Microsoft Entra ID can protect against password threats, one of the reasons is that it is integrated with an effective smart lockout and password protection feature. This feature allows MS Entra ID to protect accounts from brute-force and password spray attacks through smart lockout, which temporarily blocks repeated failed sign-in attempts.
Additionally, the password protection feature in Entra ID enforces the use of strong, unique credentials by comparing new passwords against a list of banned or commonly used ones (including those from leaked credentials). These protections can extend to hybrid environments, applying consistent rules across both cloud and on-premises Active Directory.
Single Sign-On (SSO)
Microsoft Entra ID is also integrated with the Single Sign-On (SSO) feature that lets users sign in once and gain seamless access to multiple applications and resources, ranging from Microsoft 365 to thousands of supported third-party SaaS applications. To make this happen, the Microsoft Entra ID manages token exchanges in the background, eliminating repeated login prompts and improving productivity while maintaining security. This unified sign-in experience is central to modern workforce identity, ensuring secure yet frictionless access.
Application and API authentication with Microsoft Entra ID
If you are a developer, data analyst, or DBA, you might want to ask, how does the Microsoft Entra ID work with applications and API authentication?
MS Entra ID provides secure ways to authenticate applications and services against APIs, including Microsoft Graph, Azure SQL, and custom APIs. However, this security method requires you to register your application and leverage the OAuth 2.0 flows.
Here is how this process works in real-world scenarios.
Registering an app in Microsoft Entra ID
To enable your application or API authentication with Microsoft Entra ID, you must first register the app. The registration process establishes an identity for your app, enabling it to request tokens and access APIs. Follow the steps below to register your app with MS Entra ID:
- Sign in to the Microsoft Azure portal.
- Among the list of options on the left sidebar, choose Microsoft Entra ID.
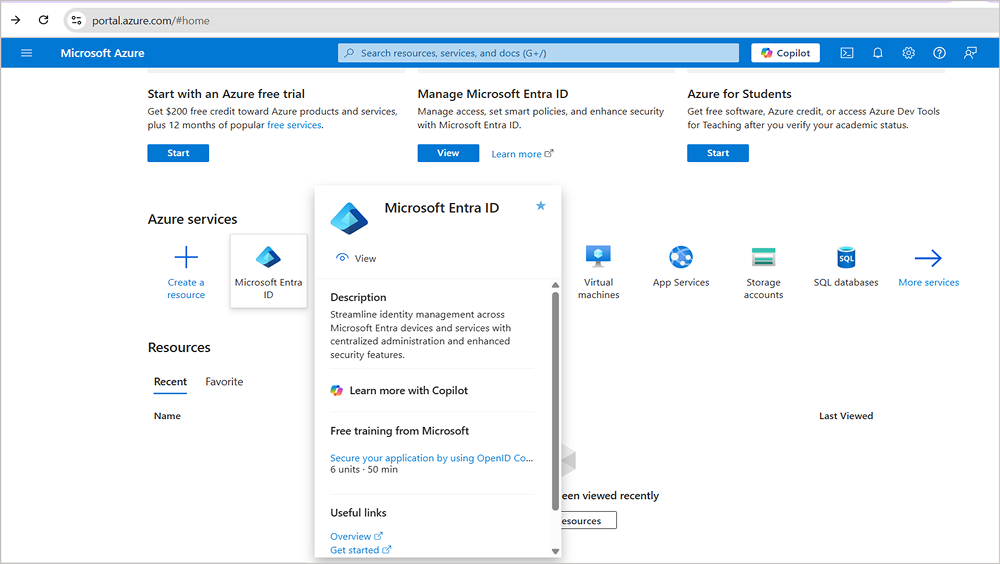
- Select Add, and choose App registration.
- In the App registration page, provide your application name and select the supported account type or who can use the app (single tenant, multi-tenant, or personal Microsoft accounts).
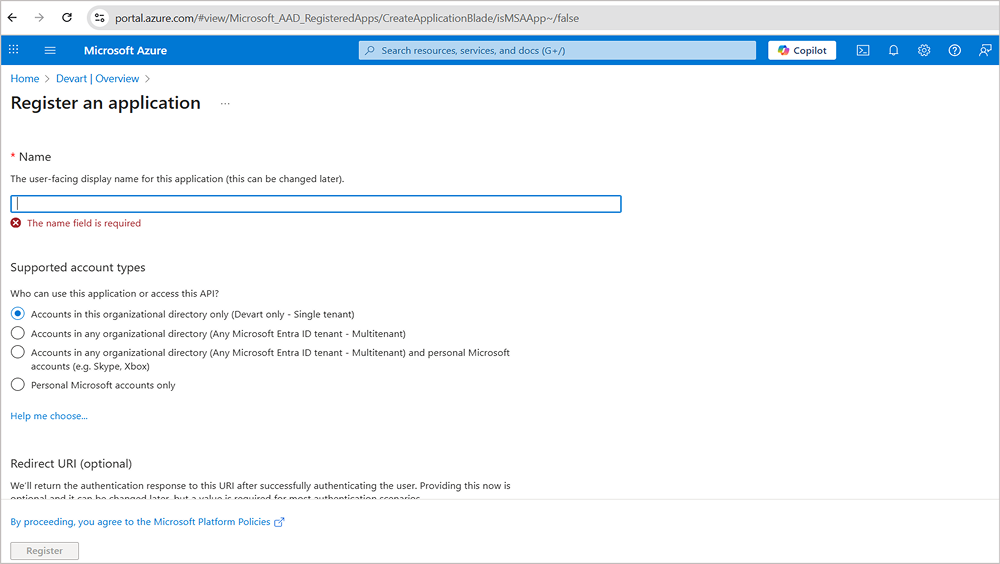
- For web or native apps, configure redirect URIs where Entra ID will send tokens after successful login.
- Choose which APIs the app needs to access (e.g., Microsoft Graph, Azure SQL). Permissions can be delegated (on behalf of the user) or application-level (daemon/service).
- For non-interactive flows, generate credentials that the app can use to authenticate securely.
- Set platform details (web, mobile, desktop), enable implicit grant if needed, and enforce conditional access policies.
Note
Registering your application allows you to integrate it with Microsoft Entra ID’s identity system, handling token issuance and access control centrally and securely.
OAuth 2.0 authentication flows
While registering your application, you will be required to configure the authentication method you want. Here is a breakdown of the OAuth 2.0 authentication methods that Microsoft Entra ID supports, each suited to different types of applications.
Authorization code flow (for web apps)
This flow is designed for server-side web applications that can securely store credentials. Here is how it works:
- You try to access a web app and you’re redirected to Microsoft Entra ID’s sign-in page.
- After successful sign-in (and MFA, if required), Entra ID sends an authorization code back to the client web app via your browser’s redirect.
- The web app’s server-side back end securely sends the authorization code (plus its credentials) to Entra ID and requests tokens.
- Entra ID returns an access token (and often a refresh token). The web app then uses the access token to call APIs or access the protected resources that you want, e.g., Azure SQL.
The authorization request from the client app to Microsoft Entra ID for an access token would look like this:
GET https://login.microsoftonline.com/{tenant}/oauth2/v2.0/authorize
?client_id={client_id}
&response_type=code
&redirect_uri={redirect_uri}
&scope=api://your-api/.default Here is an example of what the redirect from Entra ID looks like:
HTTP/1.1 302 Found
Location: https://myapp.com/auth/callback
?code=0.AAA5uY...QdX9vJk.9LhXwA...
&state=12345 Device code flow (for CLI tools)
This flow is ideal for command-line tools, IoT devices, or any environment where a browser isn’t available. Instead of signing in directly in the client application, you are shown a short device code and a URL.
Here is a simplified flow of how this works in real life:
- The CLI tool (or IoT device) asks Microsoft Entra ID for a device code and shows this to you, along with a URL (e.g., https://microsoft.com/devicelogin).
- Then you open the URL in a browser on a phone or PC, enter the device code, and sign in with Entra ID credentials (including MFA if required).
- After successful authentication, Entra ID connects your verified session with the device code the app was given earlier.
- The CLI tool or device gets back an access token (and possibly a refresh token), which it can now use to call APIs or access resources securely.
Example of the request the client app sends to ask Microsoft Entra ID for a device code and a verification URL.
POST https://login.microsoftonline.com/{tenant}/oauth2/v2.0/devicecode
client_id={client_id}
scope=api://your-api/.default Example of response from Entra ID containing the requested device code and a verification URL.
{
"device_code": "GmRhmzDdjI2jCNh3aSjCoJpH0xVj7Rli1a0m...",
"user_code": "F7J3K9",
"verification_uri": "https://microsoft.com/devicelogin",
"expires_in": 900,
"interval": 5,
"message": "To sign in, use a web browser to open https://microsoft.com/devicelogin and enter the code F7J3K9 to authenticate."
} Client credentials flow (for daemons/services)
This flow is designed for background services, daemons, or server-to-server processes that run without any user interaction. Instead of prompting a user to sign in, the application authenticates directly with Microsoft Entra ID using its client ID and a trusted credential.
Here is a simplified flow of how this works:
- The background service or daemon sends a request to Microsoft Entra ID’s token endpoint. In that request, it includes its client ID (the app’s unique identifier) and a credential (either a client secret or a certificate.)
- Entra ID validates if the app exists in the directory, if the secret/certificate is valid, and if the app has permission to access the requested API.
- If validation passes, Entra ID sends back an access token.
- The app then uses that access token to authenticate itself directly to APIs (for example, Microsoft Graph or a custom API)—no user ever signs in.
Here is an example of the request the client application sends to Entra ID to request an access token:
POST https://login.microsoftonline.com/{tenant}/oauth2/v2.0/token
client_id={client_id}
client_secret={client_secret}
scope=api://your-api/.default
grant_type=client_credentials The response from Entra ID containing the requested access token would look like this:
{
"token_type": "Bearer",
"expires_in": 3599,
"ext_expires_in": 3599,
"access_token": "eyJ0eXAiOiJKV1QiLCJub25jZSI6Ij..."
} Real-world use case: secure Azure SQL access via dbForge Studio
To see Microsoft Entra ID in action, let’s walk through how your organization can secure developers’ access to Azure SQL Database using dbForge Studio for SQL Server.
dbForge Studio for SQL Server is among the best SQL IDEs designed to make working with SQL Server and Azure SQL databases faster, easier, and more secure. It brings together everything you need as a database developer, administrator, or analyst in a single interface: query building, database design, administration, data comparison, source control, and robust security integration.
Additionally, the dbForge Studio security integration process with the Microsoft Entra ID combines app registration, modern authentication, and conditional access policies to protect sensitive data while keeping your experience smooth.
Here is a step-by-step breakdown of how this process works with the Azure SQL database.
- To create an app identity, define redirect URIs, and assigns delegated permissions for Azure SQL database login access, you will first register dbForge Studio for SQL Server in Microsoft Entra ID as a native client application. Check the Application and API authentication with Microsoft Entra ID section above for how to complete this action.
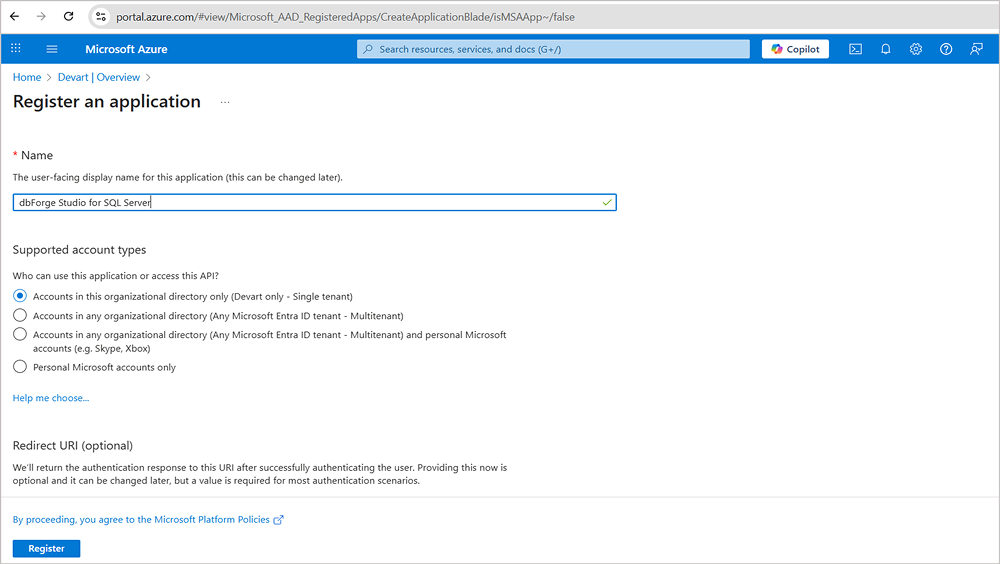
- After registration, enforce MFA to prevent credential theft. This process ensure that every developer that wants to use the app must verify logins with the Microsoft Authenticator app, SMS, or biometric checks.
- Apply conditional access that evaluates signals like device compliance, location, and risk. For example, logins from unmanaged devices or untrusted geographies are blocked, while sign-ins from compliant corporate laptops require MFA.
- After you have completed this action, when a developer opens dbForge Studio for SQL Server and attempts to connect to Azure SQL database, the following happens:
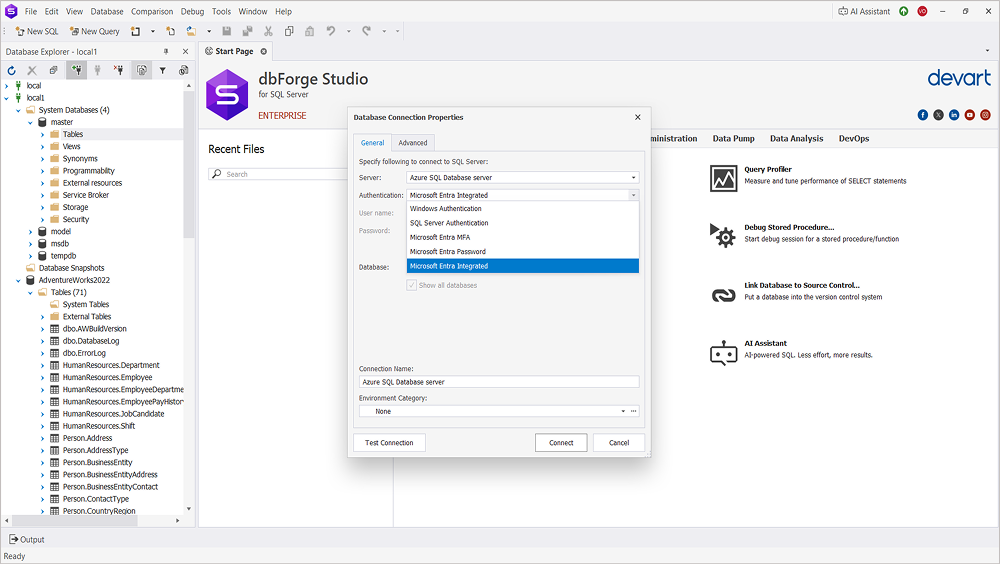
- The app redirects them to Microsoft Entra sign-in.
- The user enters organizational credentials.
- Entra ID enforces the MFA challenge before granting access.
- dbForge Studio receives a token and uses it to establish a secure connection to Azure SQL.
Connection experience: from the developer’s perspective, the login is very seamless. dbForge Studio for SQL Server uses Active Directory Integrated Authentication, which implies that it relies on the user’s existing domain credentials instead of storing separate database passwords. After entering credentials, the MFA prompt appears (for example, approving a notification in Microsoft Authenticator). Once verified, dbForge Studio automatically establishes a secure connection to Azure SQL. No manual password management is required.
Compliance benefits: this approach strengthens security controls in ways that directly support compliance frameworks like GDPR, SOC 2, ISO 27001, and others. By enforcing MFA, conditional access, and token-based authentication, dbForge Studio for SQL Server demonstrates strong identity governance, reduces exposure to insider and external threats, and ensures database access is tightly audited and monitored.
Ready to experience a better way to work with SQL Server? Download dbForge Studio for SQL Server and see how it transforms database development and administration.
Conclusion
Microsoft Entra identity method combines a strong collection of verification and authentication tools that aligns with today’s Zero Trust security. Entra ID lets you safeguard users, apps, and data from all kinds of threats in a very flexible way. From the classic username and password logins to more advanced options like passwordless authentication, MFA, and conditional access, Entra provides different options to secure your credentials. Also, it supports widely used protocols such as OAuth 2.0 and OIDC, ensuring safe access and token-based verification across cloud and hybrid environments.
These features are directly useful for database experts in their daily work. Entra ID authentication works with tools like dbForge Studio for SQL Server, which lets you connect to Azure SQL databases securely without having to use hard-coded or shared passwords.
dbForge Studio for SQL Server is not just for writing queries. It’s a professional-grade tool that reduces complexity, strengthens security, and gives your team the confidence to manage both on-premises SQL Server and Azure SQL workloads effectively.
Download the dbForge Studio for SQL Server and try it out for free.
FAQ
1. What is Microsoft Entra ID, and how is it used for authentication?
Microsoft Entra ID (formerly Azure Active Directory) is Microsoft’s cloud-based identity and access management platform. It authenticates users, secures applications, and enables modern login methods such as MFA, passwordless sign-ins, and single sign-on.
2. Which authentication methods are supported in Microsoft Entra ID?
MS Entra ID supports a wide range of methods, including username and password, multi-factor authentication (MFA), Integrated Windows Authentication (IWA), Windows Hello for Business, the Microsoft Authenticator app, and FIDO2 security keys.
3. How does multi-factor authentication (MFA) work in Microsoft Entra ID?
MFA requires users to verify their identity with two or more factors, such as a password plus a one-time code, a phone call, or a push notification in the Microsoft Authenticator app, adding a strong layer of security.
4. What passwordless authentication options are available in Entra ID?
Passwordless options include Windows Hello for Business (biometric/PIN sign-in), the Microsoft Authenticator app, and FIDO2 security keys. These methods reduce password risks while improving user convenience.
5. How do FIDO2 security keys and the Microsoft Authenticator app work with Entra ID?
- FIDO2 keys let users authenticate by tapping a physical security device and entering a PIN; no password is required.
- Microsoft Authenticator turns a phone into a secure credential, where users approve sign-in requests with a simple tap.
6. What is token-based authentication in Microsoft Entra, and why is it important?
Token-based authentication (via OAuth 2.0 and OpenID Connect) issues secure tokens after a successful sign-in. Apps and APIs then validate these tokens instead of passwords, enabling modern, scalable, and secure authentication across cloud services.
7. How are conditional access policies applied in Microsoft Entra ID?
Conditional access evaluates factors such as user identity, device health, location, and risk signals before granting access. For example, an employee logging in from an unknown country may be forced to complete MFA before accessing company data.
8. Do I need to register an application to use Entra ID authentication?
Yes, applications that need to integrate with Entra ID, such as a custom web app, must be registered. Registration defines redirect URIs, permissions, and how the app interacts with tokens and APIs.
9. How can I connect to an Azure SQL Database using Microsoft Entra ID?
You can connect by registering your SQL client (like dbForge Studio) in Entra ID, enabling MFA, and applying conditional access policies. Once configured, developers can log in securely with their Entra credentials instead of SQL passwords.
10. What’s the difference between Entra password, integrated, and MFA login methods?
- Password login: traditional username + password entry.
- Integrated login: seamless domain-joined authentication (no prompts inside corporate networks).
- MFA login: requires additional verification (app, SMS, or call) to confirm the user’s identity.

