Navigating the security landscape of cloud services can be complex, but AWS IAM provides a robust framework for secure access management. In this article, we’ll explore what AWS Identity and Access Management (IAM) is and how it enhances security. We’ll also provide a step-by-step guide on connecting to Amazon Relational Database Service (RDS) using IAM for database authentication, ensuring that your database interactions are both secure and streamlined.
Content
- What is IAM?
- How to set up IAM DB authentication
- How to connect to AWS RDS using dbForge Studio for MySQL
- Summary

What is IAM?
IAM, or Identity and Access Management, is a web service provided by Amazon Web Services (AWS) that helps you securely control access to AWS resources. It allows you to manage users, security credentials such as access keys, and permissions that control which AWS resources users and applications can access.
In simple words, the IAM authentication enables database connection via an authentication token, which is produced using an IAM policy associated with a specific role or user. The authentication token is valid for 15 minutes.
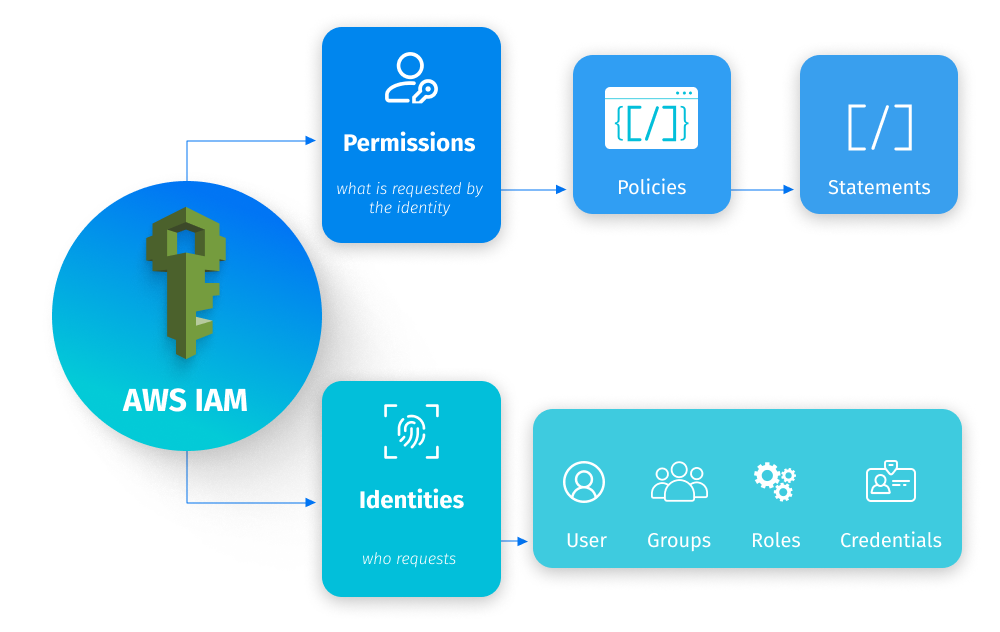
Benefits of AWS IAM
IAM is crucial for managing the security of your AWS environment. It allows for granular control over who can access what resources, under what conditions, and with what permissions. This is important not only for secure system architecture but also for compliance with regulatory requirements. IAM services are offered at no additional charge and are implemented across your entire AWS account. Other benefits of AWS IAM include:
- Multi-Factor Authentication (MFA): AWS IAM allows you to enhance security by requiring users to provide not just a password but also a second factor of authentication, which significantly reduces the likelihood of unauthorized access.
- Roles and temporary credentials: You can assign roles to users and applications within your own organization or to users from third-party accounts. This way, you can grant permissions that are temporary, limiting access only for a required duration.
- Federated access: With AWS IAM, you can allow users who already have passwords elsewhere—like in your corporate directory—to use that identity to access AWS Management Console or call AWS APIs without IAM user credentials.
- Identity federation: You can connect IAM with external identity providers such as Active Directory or any provider that supports SAML 2.0. This removes the need to create separate IAM users for each entity needing access to your AWS environment.
- Integration with AWS Services: IAM is integrated with all AWS services, so you can define roles and permissions to control access to any service or application running on AWS.
- Security by default: New users have no access to AWS resources until permissions are explicitly granted, following the security principle of “least privilege.”
How AWS IAM works
IAM provides the infrastructure necessary to control authentication and authorization for your AWS account.
Initially, when a person or an application attempts to access AWS, they need to prove their identity by presenting their login details. This step, known as authentication, involves verifying the credentials against an identity recognized by AWS, such as an IAM user, an IAM role, a federated user from an external identity provider, or an application configured with AWS security credentials.
Following successful authentication, the entity then seeks permission to use AWS resources. This is where authorization comes into play. It’s a process where AWS evaluates if and how an authenticated identity is allowed to interact with specific services or resources. For instance, after logging into the AWS Management Console, you’re not immediately interacting with any AWS services. But as soon as you navigate to a particular service, an authorization check determines if your identity has the necessary permissions, according to the applicable policies, to use that service. These authorization requests can be made by principals within your AWS account or from another AWS account that you trust.
Once the authorization is confirmed, the identity is then able to execute various tasks within the AWS environment. These tasks might range from launching instances in Amazon EC2 and adjusting IAM group configurations to managing the lifecycle of S3 buckets, depending on the permissions granted.
Components of AWS IAM
AWS Identity and Access Management (IAM) is composed of several key components that work together to manage access to AWS services and resources securely. The key components of AWS IAM comprise:
IAM users
Users are the individual identities created in IAM, each with their unique set of credentials. These credentials can be used to authenticate a real person or an application when interacting with AWS services. Each user can be given specific permissions to control what actions they are allowed to perform within AWS. This granularity ensures that every user operates under the principle of least privilege, accessing only the resources necessary for their role.
IAM groups
Groups serve as collections of users, simplifying the permission assignment process. Instead of attaching policies to each user individually, you can create a group, apply the necessary permissions to this group, and then add users. Any permissions assigned to a group automatically apply to all users within that group. This not only streamlines the management of user permissions but also makes it easier to update permissions for multiple users simultaneously.
IAM roles
Roles in IAM are designed to delegate permissions for specific tasks. Unlike users, roles do not have a permanent set of credentials. Instead, roles provide temporary security credentials that can be assumed by trusted entities, such as AWS services, applications, or users from different AWS accounts. This is particularly useful when an application needs to perform actions in AWS on your behalf or when you need to grant access to users from other AWS accounts temporarily.
IAM policies
Policies are the documents that define permissions within IAM. Written in JSON, these documents specify the actions allowed or denied for users, groups, or roles. Policies can be fine-tuned to control access to specific AWS services or resources and can include conditions for when and how permissions apply. This detailed level of control is key to protecting resources and ensuring users can perform only the actions they need to fulfill their job responsibilities.
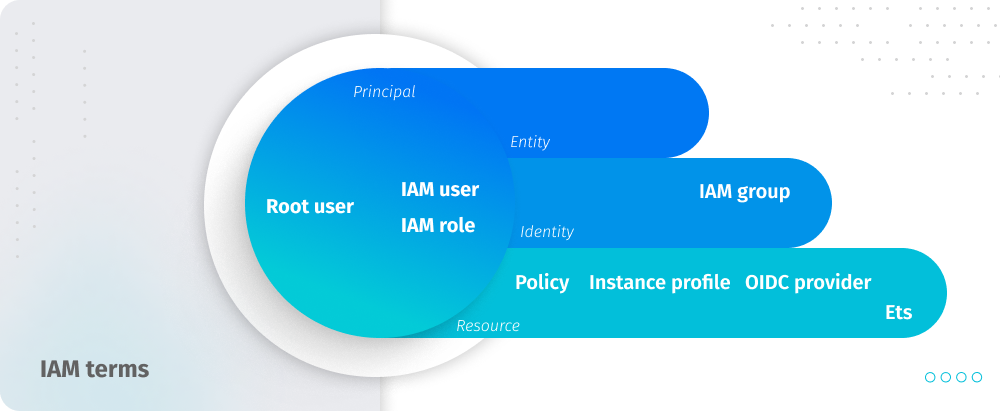
Features of IAM
- Granular permissions. IAM allows organizations to assign granular permissions to users, groups, roles, and resources, controlling who is allowed to take what actions with detailed precision.
- Multi-Factor Authentication (MFA). IAM supports MFA, adding an extra layer of security on top of username and password.
- Identity federation. IAM permits identity federation, allowing users to authenticate using an external identity provider instead of IAM credentials. This facilitates single sign-on (SSO) capabilities, enabling users to log in once and access multiple AWS services.
- Roles for cross-account access. Roles can be created to delegate permissions to users, applications, or services that need to perform actions on your behalf. This feature is particularly useful for providing access to users from one AWS account to resources in another AWS account.
- Policy simulator. IAM includes a policy simulator tool that helps administrators understand and test the effects of their permission policies, ensuring they work as intended before going live.
- Access Advisor. IAM Access Advisor shows the service permissions granted to a user and when those services were last accessed, providing insights for tightening permissions based on actual usage.
- Access Analyzer. This feature helps to identify the resources in your organization and accounts, such as S3 buckets or IAM roles, that are shared with an external entity.
- Customizable password rotation policies. Administrators can enforce password complexity requirements and rotation policies, improving account security.
- Compliance with PCI DSS. The Payment Card Industry Data Security Standard (PCI DSS) represents a set of requirements designed to ensure that all companies processing, storing, or transmitting credit card information maintain a secure environment. IAM adheres to this standard.
Limitations of IAM authentication for MariaDB, MySQL, and PostgreSQL
Connection throttling: IAM database authentication may not be suitable if your application demands more than 200 new connections per second.
Authentication token size considerations: The size of an IAM database authentication token is influenced by various factors, including the number of IAM tags, the specifics of IAM service policies, the lengths of ARNs (Amazon Resource Names), and other related IAM and database properties. While the minimum size of this token is typically around 1 KB, it can be larger depending on these factors. It’s important to verify that your database driver (such as ODBC) and any tools you use can handle the token’s size without limitations. If a token is truncated, it will render it invalid for the authentication process as the database and IAM will fail to verify it.
SSL/TLS requirement: IAM database authentication requires an SSL connection to the database. You must ensure that your database connection is configured to use SSL, or the authentication process will fail.
Authentication precedence in PostgreSQL: For instances running PostgreSQL, if the rds_iam role is associated with a user, including the RDS master user, IAM authentication will take precedence over password authentication. Consequently, this user must authenticate as an IAM user. This means that once IAM authentication is enabled for a user, you must use the IAM method for logging in, as password verification will no longer be applicable for that user.
Exclusivity of IAM and Kerberos authentication: On Amazon RDS for PostgreSQL, there is a limitation that prevents the simultaneous use of IAM and Kerberos authentication methods. If you enable IAM authentication, you cannot use Kerberos, and vice versa. This exclusivity requires a choice between one of the two authentication methods when configuring your RDS instance for PostgreSQL.
IAM authentication and replication: With PostgreSQL on Amazon RDS, IAM authentication cannot be used for establishing replication connections. This means that for any operation that requires database replication, you’ll need to rely on traditional password authentication or other supported methods, rather than IAM, to set up and manage replication processes.
Region availability: IAM database authentication is available only in certain AWS regions, so you need to ensure that it’s supported in the region where your RDS instance is deployed.
AWS RDS versions: IAM authentication is only supported with specific versions of MySQL that are compatible with the AWS RDS platform. You need to verify that your MySQL version supports IAM authentication.
How to set up IAM DB authentication
Create an IAM database
To begin with, sign in to AWS Management Console. Then navigate to RDS Dashboard, choose the AWS region in which you want to create the database, and click Create database.
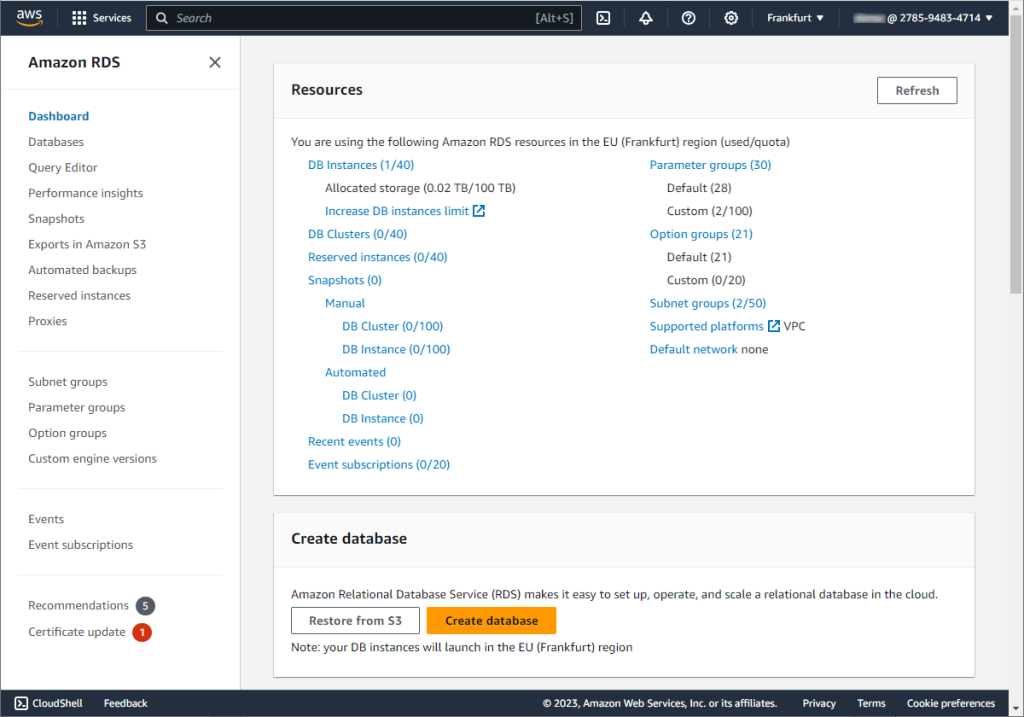
Alternatively, you can create a database from the Databases section.
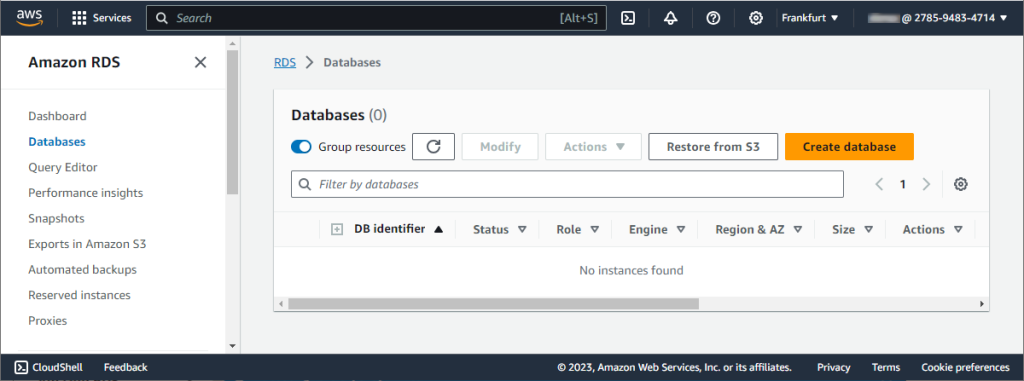
The Create database page opens. Click Easy create and in Configuration, select MySQL.
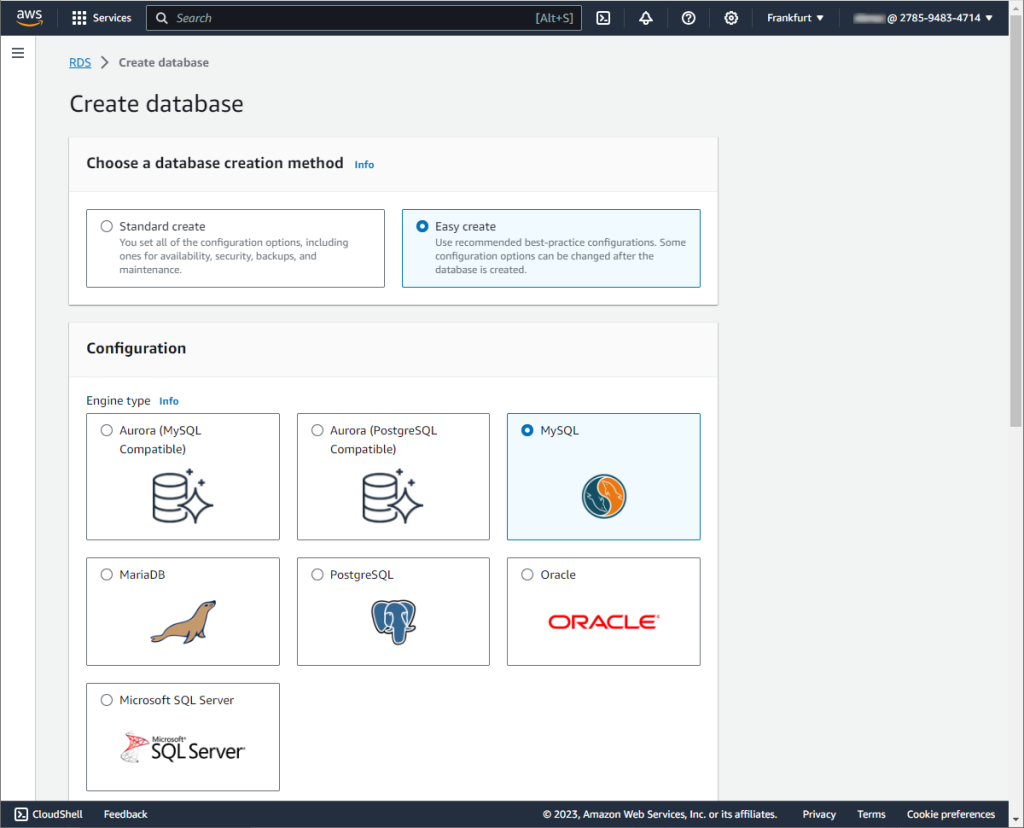
Next, for DB instance size, select Free tier. For DB instance identifier, enter the desired database identifier. And for Master username, enter a name for the master user, or keep the default name.
For the database to have a master password created automatically, select the Auto generate a password option. If you prefer to set your own master password, ensure that the Auto generate a password option is not selected, then input your chosen password into both the Master password and Confirm master password fields.
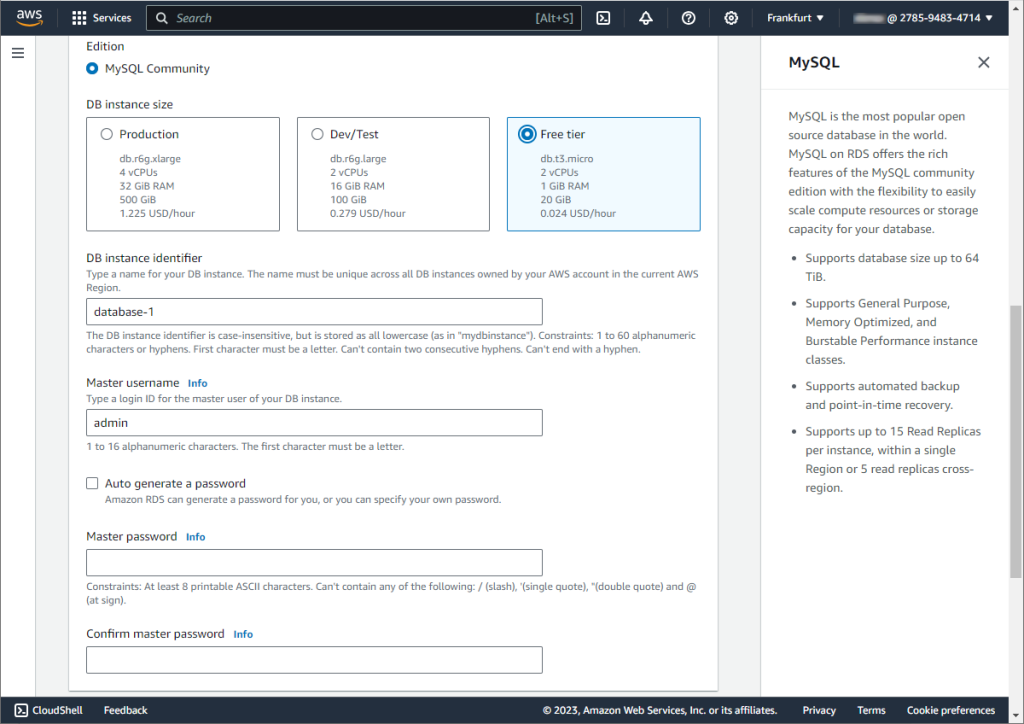
Once done, click Create database. The newly created database will appear on the Databases list. Note that it can take up to 20 minutes before the new database is available.
To learn more on how to deploy a MySQL database instance on Amazon RDS, refer to Connecting to Amazon RDS MySQL Database.
Enable IAM DB authentication on the database
Now that we have created a new database, we need to enable IAM database authentication on it.
- In the navigation pane, select Databases.
- Choose the DB instance that you want to enable IAM authentication on.
- Click Modify.
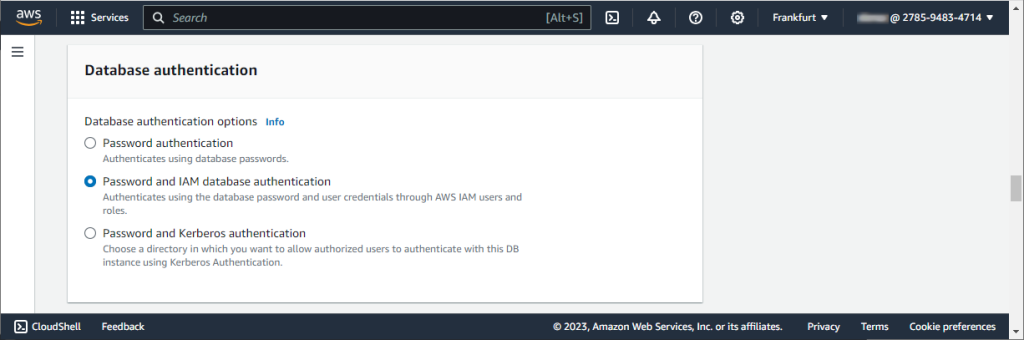
4. The Modify DB instance page opens. Scroll down to the Database authentication section and click to select Password and IAM database authentication.
Create a database user account that uses an AWS authentication token
Run the following SQL command to create a new user that uses AWS IAM authentication tokens.
CREATE USER 'new_user'@'%' IDENTIFIED WITH AWSAuthenticationPlugin AS 'RDS';Replace new_user with your desired username.
Create an IAM Policy
Now you need to create an IAM policy that maps the database user to the IAM role. For this, navigate to Identity and Access Management (IAM). Then, in the navigation pane, select Policies and click Create policy.
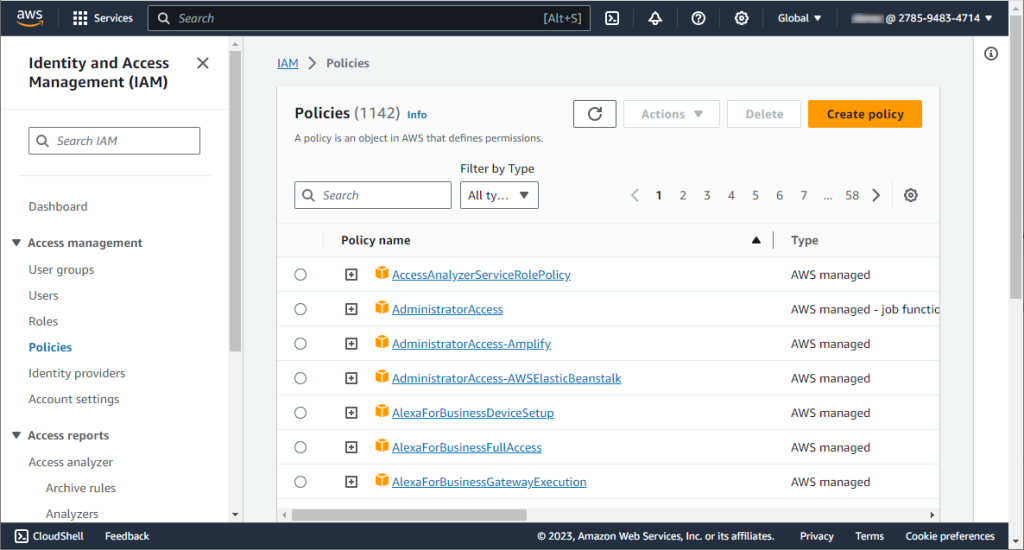
The Create policy page opens. Go to the JSON tab to enter the policy.
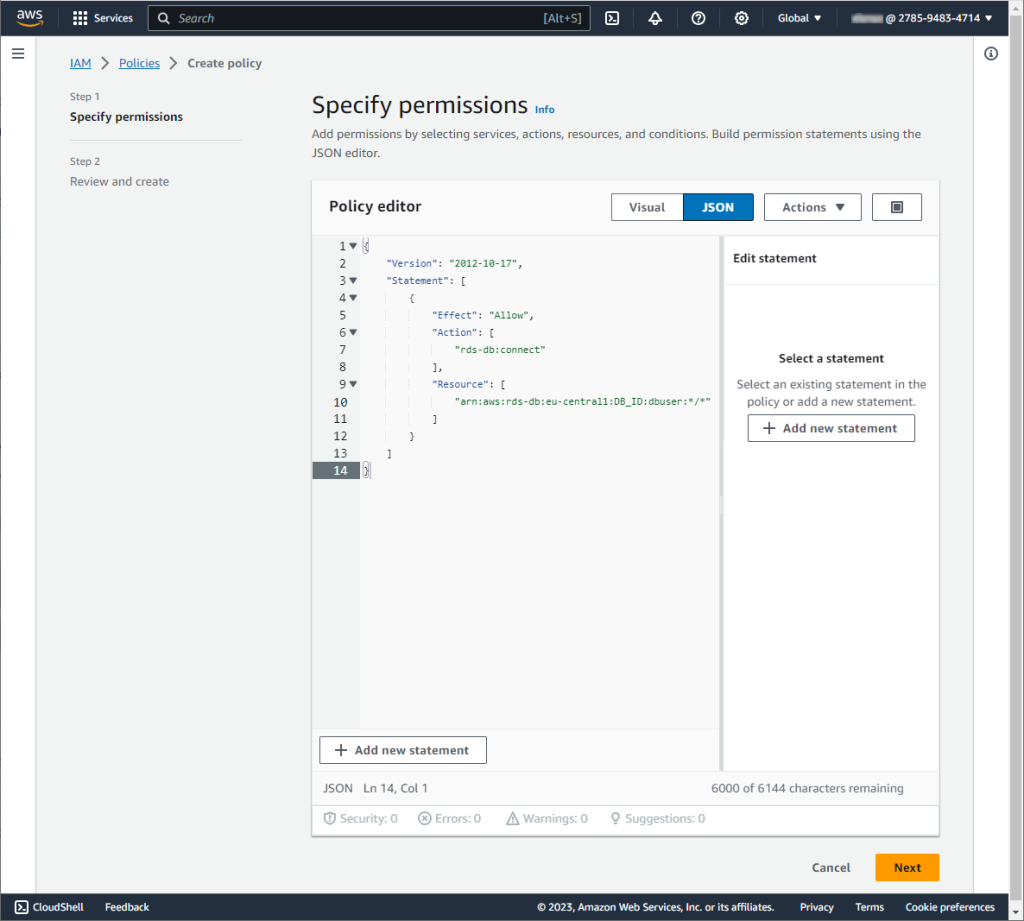
The policy example presented in the image above comprises a single statement and is structured as follows:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "rds-db:connect",
"Resource": "arn:aws:rds-db:region:account-id:dbuser:db-instance-identifier/database-username"
}
]
}It consists of the following elements:
Effect: Specify Allow to grant access to the database. If the access is not specified explicitly, it is denied by default.
Action: Specify rds-db:connect to allow connections to the database.
Resource: Define an Amazon Resource Name (ARN) that uniquely identifies a single database account on a specific database.
Replace region, account-id, db-instance-identifier, and database-username with your actual AWS region, your AWS account ID, your RDS instance identifier, and the database username you want to map to the IAM role.
Once done, click Next.
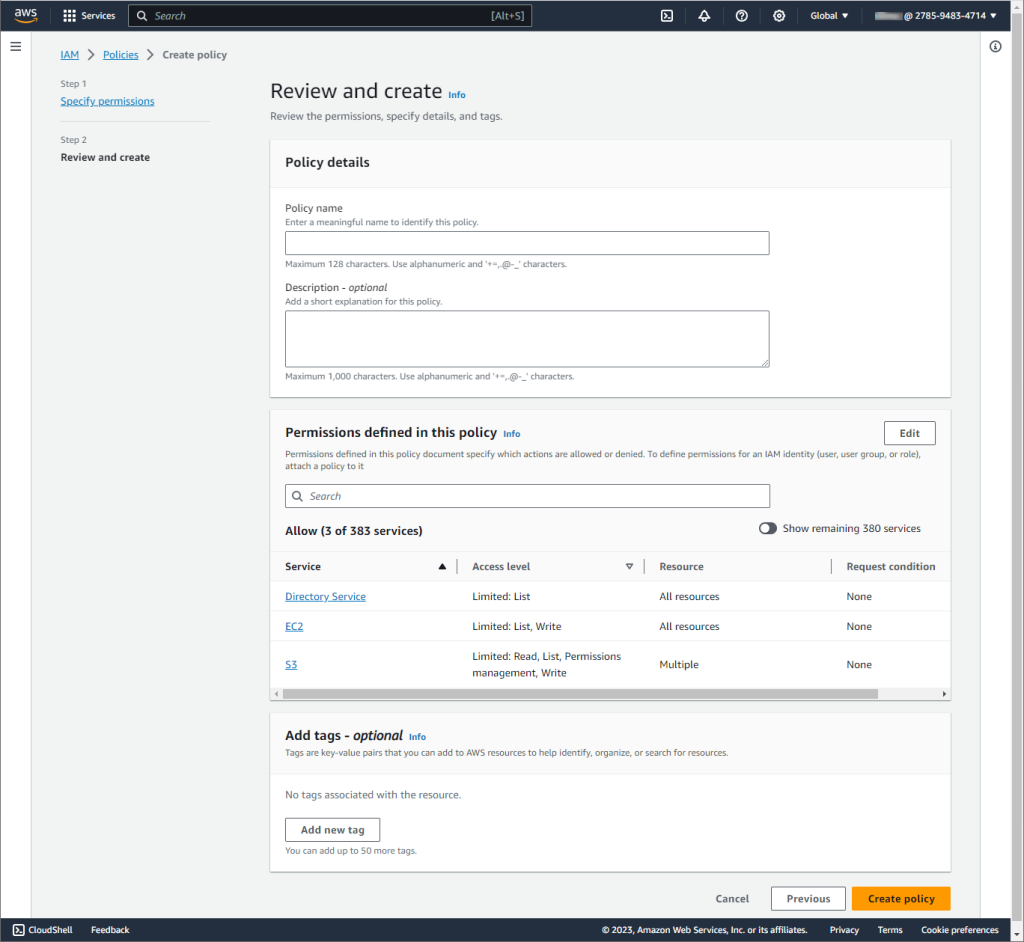
On the next page, give your policy a meaningful name and description. Then, click Create policy to save it.
Create an IAM Role
Navigate to Identity and Access Management (IAM). Then, in the navigation pane, select Roles and click Create roles.
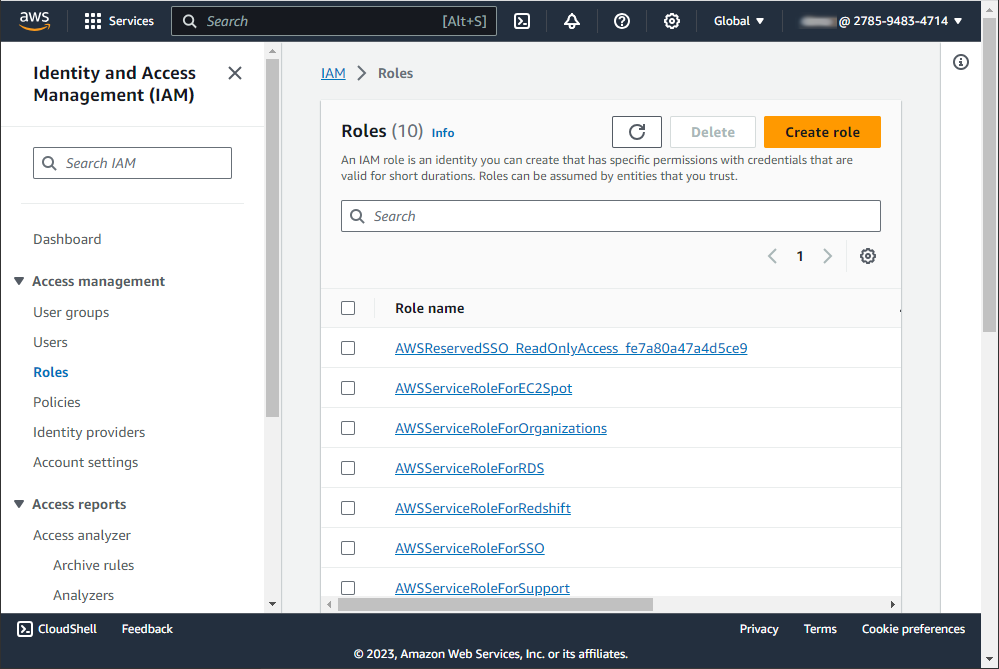
The Create role page opens. Select the type of trusted entity for the role. This could be AWS service, another AWS account, a web identity (like Google, Facebook, Amazon), or SAML 2.0 federation. We select AWS account here.
To create a role for your account, select This account. To create a role for another account, select Another AWS account and enter its Account ID. Optionally, if you want to require the users from the other account to use a Multi-Factor Authentication (MFA) token, select the Require MFA checkbox. Once done, click Next.
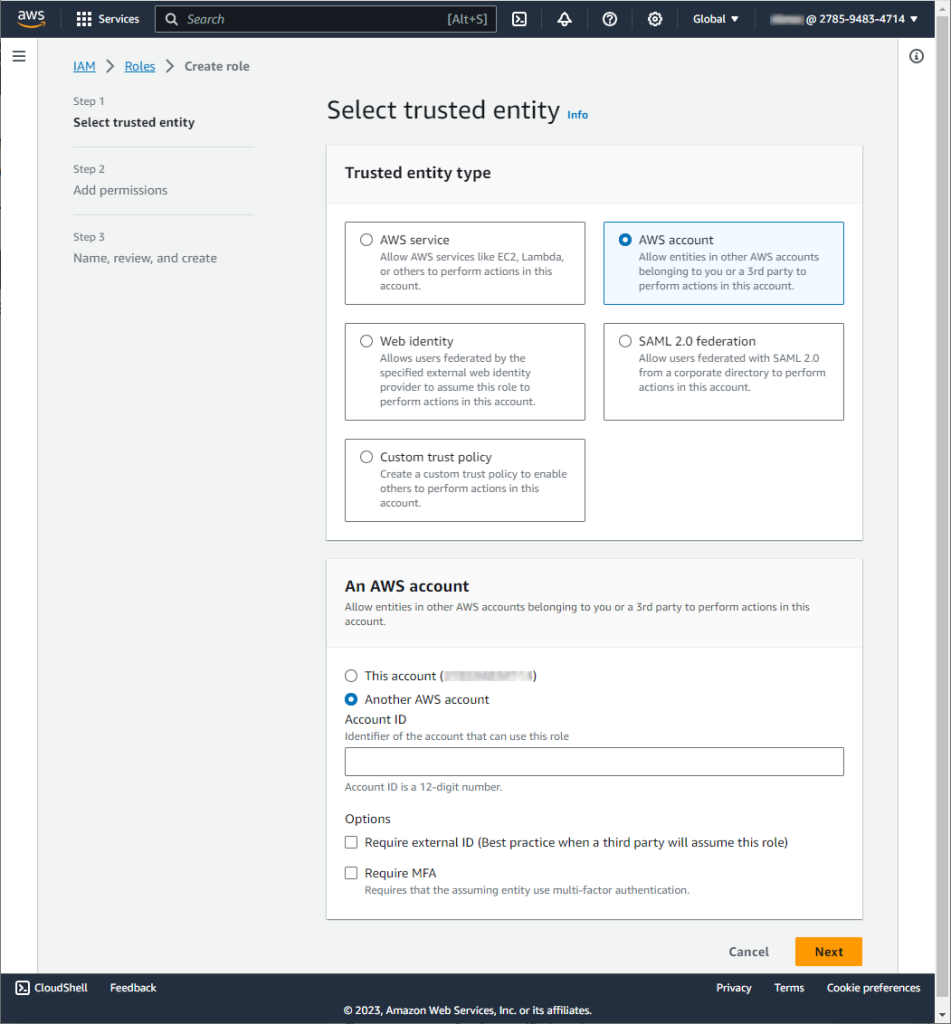
In the Add permissions step, select the policy you created earlier. Once done, click Next.
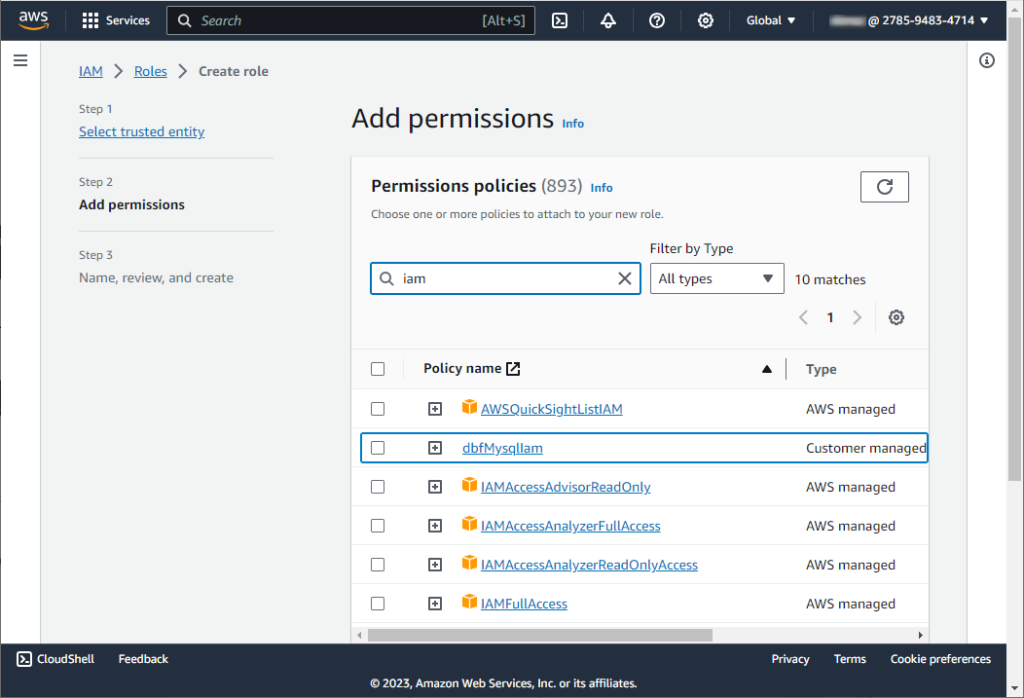
In step 3, give your role a meaningful name and a description. This will help you and others understand the purpose of the role in the future. Once you have reviewed the settings and are sure they are correctly configured, click Create role.
Note
In AWS, while it’s possible to attach IAM policies directly to an individual IAM user, best practices suggest using roles to assign permissions. This approach promotes more flexible and secure management of permissions, especially when scaling or managing multiple users.
How to connect to AWS RDS using dbForge Studio for MySQL
You can connect to AWS RDS using dbForge Studio for MySQL, which is an advanced tool for database management, development, and administration. This powerful IDE facilitates an effortless and efficient management experience for your MySQL and MariaDB databases on the AWS cloud platform. If you’re looking for instructions on how to connect to Amazon RDS MariaDB or how to connect to Amazon RDS MySQL, this tool provides a simple and user-friendly approach.
Step 1: Generate an IAM authentication token
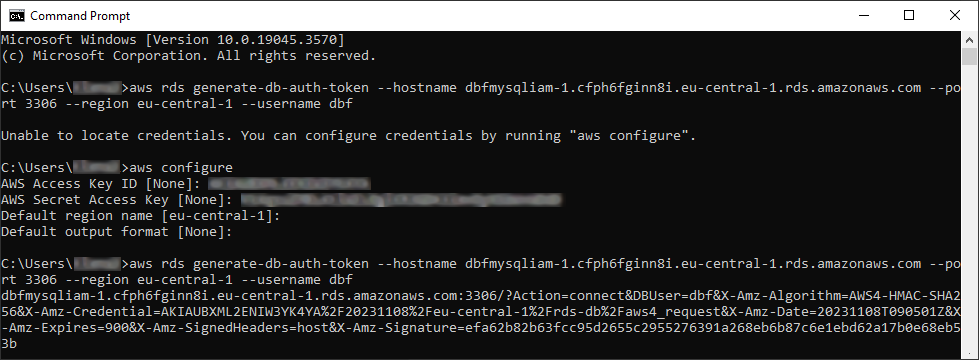
To generate an authentication token for RDS, you typically use the AWS Command Line Interface (CLI). The authentication token is used in place of a password when you connect to an RDS database instance.
- Install the AWS CLI: If you haven’t already, you need to install the AWS CLI on your local machine. You can download it from the AWS website.
- Configure the AWS CLI: Run
aws configureto set up your AWS credentials (access key ID and secret access key), default region, and output format.
Note
To acquire an access key ID and secret access key, navigate to the user’s details page within the IAM dashboard. Then, in the Summary section, click Create access key to generate the credentials. - Generate an authentication token:
- Use the following AWS CLI command to generate an authentication token:
aws rds generate-db-auth-token --hostname <db-instance-endpoint> --port <db-port> --region <aws-region> --username <db-username>- Replace
<db-instance-endpoint>with your RDS instance endpoint. - Replace
<db-port>with the port your database uses (the default for MySQL is 3306). - Replace
<aws-region>with your RDS instance’s AWS region. - Replace
<db-username>with the database username.
Step 2: Connect to the AWS RDS instance using dbForge Studio for MySQL
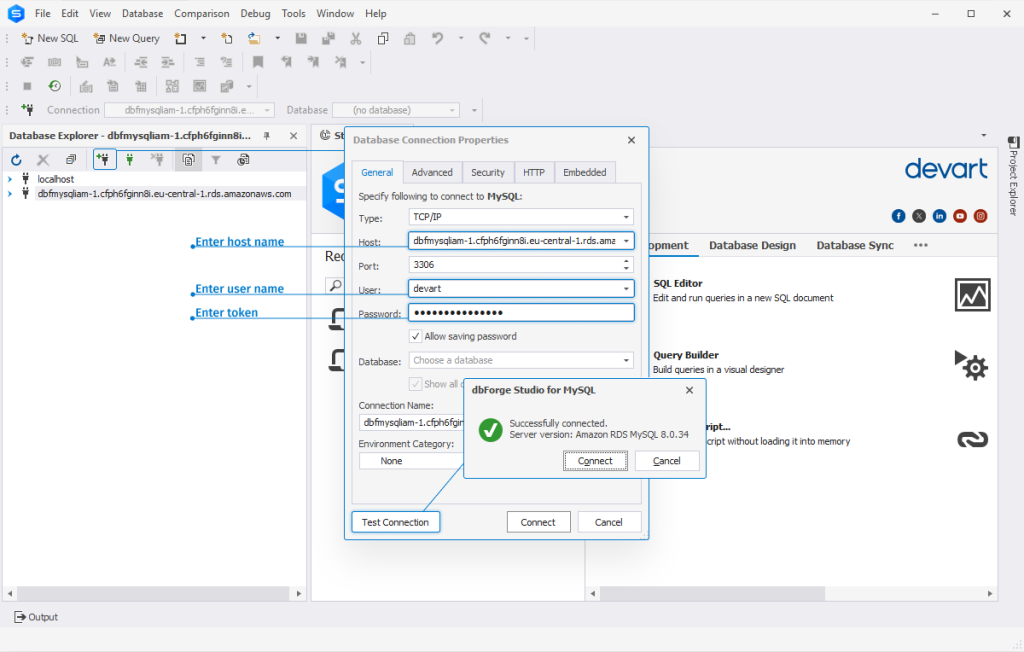
- Download dbForge Studio for MySQL and install it.
- Run the Studio and click New Connection.
- In the Database Connection Properties dialog that opens, go to the Security tab and enable SSL security protocol.
- On the General tab of the Database Connection Properties dialog, enter the host name, the user name, and the token you have generated in Step 1.
- Optional: Click Test Connection to ensure that your settings are correct.
- Click Connect.
Summary
AWS Identity and Access Management (IAM) ensures the secure management of AWS resources, with granular control over users, roles, permissions, and added security through Multi-Factor Authentication and federated access.
The article includes a tutorial on setting up IAM database authentication, creating IAM policies, roles, and connecting to the RDS instance using an authentication token. It also demonstrates the ease of connecting to Amazon RDS via IAM tokens using dbForge Studio for MySQL.
Ready to streamline your Amazon RDS processes? Download dbForge Studio for MySQL and leverage its advanced features for an enhanced database management experience.


